Table of Contents
RAN Checklist
This page is designed to describe all check points to perform before and after installing RAN packages for a RAN platform connectivity.
Before installing RAN packages (preconditions)
Here are the needed artefacts to install RAN packages on your gateway operating system.
The recommended package version number to use for a RAN platform compatibility is indicated in the Compatibility Matrix.
| Step | Needed Artefact | Verification (OK/KO) |
|---|---|---|
| 1 | Compatibility Matrix |
| Step | Needed Artefacts | Verification (OK/KO) |
|---|---|---|
| 2 | BSCC package / Compatibility Matrix | |
| 3 | SNMP package / Compatibility Matrix | |
| 4 | OPENVPN package / Compatibility Matrix |
| Step | Needed Artefacts | Verification (OK/KO) |
|---|---|---|
| 5 | LIBLORAGW (HAL) package version / Compatibility Matrix | |
| 6 | PACKET FORWARDER package version / Compatibility Matrix |
ping 8.8.8.8 command to your gateway's operating system.
After installing RAN packages (postconditions)
Here are the list of operations to perform to check that the install process has been correctly done.
| Step | Check operation | Verification (OK/KO) |
|---|---|---|
| 1 | Check install of RAN packages | |
| 2 | Check firewall rules | |
| 3 | Check RAN processes run | |
| 4 | Check RAN/VPN connection (ifconfig) | |
| 5 | Check VPN Server access | |
| 6 | Check SNMP access | |
| 7 | Check LNS access | |
| 8 | Check RAN/VPN connection (dashboard) | |
| 9 | Check Packet Forwarding (logs) | |
| 10 | Check Packet Forwarding (dashboard) |
1. Check install of RAN packages
Check that all packages in your gateway environnment are correctly installed.
command :
- For iBTS:
# opkg list-installed - For iFemtoCell:
# opkg list-installed - For Wirnet Station:
# get_version -u -v
expected result : All RAN packages (BSCC, SNMP, OpenVPN, HAL, SPF) have been correctly installed with the requested version.
For example (iBTS):
bscc - v2.1 kerlink-openvpn-config-pki2-klk-lpbs-060337 - 1.8 keros - 3.1.13-0-ga05e3252 libloragw2 - 4.0.1-klk3 lorasnmp - v2.1 spf2 - 4.0.0-klk9_4.0.1-klk3
2. Check firewall rules
Check that following ports accept all input and output connections from/to:
- port 1194: OpenVPN Server
- port 10161/10162: RAN BSC component (SNMP & Trap management)
- port 1700: Packet Forwarding Server
command :
'# iptables --list-rules'
expected result :
port 1194 accept I/O connections:
-A INPUT -p udp -m udp --sport 1194 -j ACCEPT
-A OUTPUT -p udp -m udp --dport 1194 -j ACCEPT
ports 10161 and 10162 accept I/O connections:
-A INPUT -p udp -m udp --sport 10161:10162 -j ACCEPT
-A OUTPUT -p udp -m udp --dport 10161:10162 -j ACCEPT
port 1700 accept I/O connections:
-A INPUT -p udp -m udp --sport 1700 -j ACCEPT
-A OUTPUT -p udp -m udp --dport 1700 -j ACCEPT
For example (iBTS):
-P INPUT DROP -P FORWARD DROP -P OUTPUT DROP -A INPUT -p udp -m conntrack --ctstate NEW,RELATED,ESTABLISHED -j ACCEPT ... -A INPUT -p udp -m udp --sport 1194 -j ACCEPT -A INPUT -p udp -m udp --sport 1700 -j ACCEPT -A OUTPUT -p udp -m udp --sport 10161:10162 -j ACCEPT -A OUTPUT -p udp -m udp --dport 10161:10162 -j ACCEPT ... -A OUTPUT -p icmp -j ACCEPT -A OUTPUT -p udp -m udp --dport 1700 -j ACCEPT -A OUTPUT -p udp -m udp --dport 1194 -j ACCEPT ...
3. Check RAN processes run
Check that the following processes are running :
command : # ps
expected result :
bscc process is running openvpn process is running snmpd process is running
spf process is running
For example (iBTS):
PID USER VSZ STAT COMMAND
1 root 1688 S init [5]
166 root 2864 S /sbin/udevd -d
811 root 17912 S {kerosd} /usr/bin/python /usr/sbin/kerosd -p -r 600
825 root 2088 S /usr/bin/kgpsd -f /etc/kgpsd.conf
904 messageb 2892 S /usr/bin/dbus-daemon --system
908 root 4492 S /usr/sbin/connmand
917 root 4660 S /usr/sbin/sshd -f /etc/ssh/sshd_config
931 ntp 5508 S /usr/sbin/ntpd -u ntp:ntp -p /var/run/ntpd.pid -g
936 root 2728 S /sbin/syslogd -n -O /var/log/messages -b 10
940 root 2728 S /sbin/klogd -n
942 root 4884 S /usr/sbin/ofonod
948 root 2964 S /usr/sbin/crond -c /etc/cron/crontabs
1002 root 2728 S /usr/sbin/ifplugd -n -I -f -d 1 -r /etc/network/ifplugd/local.action -i eth1
1008 root 13228 S /usr/bin/monit -c /etc/monitrc
1020 root 2596 S /sbin/watchdog -t 30 /dev/watchdog
1022 root 27304 S **/user/bscc/bscc -t /user/bscc**
1044 root 2744 S {start_getty} /bin/sh /bin/start_getty 115200 ttymxc0
1045 root 2976 S -sh
1416 root 2740 S {execute_spf2.sh} /bin/sh -e /user/spf2/bin/execute_spf2.sh
1418 root 52144 S **/user/spf2/bin/spf2 -g /dev/nmea1 -y**
1419 root 2964 S logger -p local1.notice -t spf2
1711 root 0 SW< [kworker/u3:7]
1715 root 0 SW< [kworker/u3:12]
1786 nobody 4952 S **/usr/sbin/openvpn --remote demoran.wanesy.fr --port 1194 --cipher AES-256-CBC --comp-lzo --remote-cert-tls server --config /etc/op**
1844 root 27944 S **snmpd -C -c snmpd.conf -f -Lo -Ddlmod,trap,klk_notifications**
1845 root 2964 S logger -p local0.notice
...
4. Check RAN/VPN connection (ifconfig)
Check that the VPN tunnel has been correctly created.
command : # ifconfig
expected result :
"tun0" or "vpn0" interface should be up. An IP adress 10.8.0.X should be assigned to this interface.
For example (iBTS):
vpn0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00\\
inet addr:**10.8.0.13** P-t-P:10.8.0.13 Mask:255.255.0.0\\
UP POINTOPOINT NOARP MULTICAST MTU:1500 Metric:1\\
RX packets:44 errors:0 dropped:0 overruns:0 frame:0\\
TX packets:205 errors:0 dropped:0 overruns:0 carrier:0\\
collisions:0 txqueuelen:100\\
RX bytes:2325 (2.2 KiB) TX bytes:21686 (21.1 KiB)\\
5. Check VPN Server access
Check you can ping the VPN Server (10.8.0.1):
command : # ping 10.8.0.1
expected result :
ping result OK
For example:
PING 10.8.0.1 (10.8.0.1): 56 data bytes 64 bytes from 10.8.0.1: seq=0 ttl=64 time=22.011 ms 64 bytes from 10.8.0.1: seq=1 ttl=64 time=22.680 ms 64 bytes from 10.8.0.1: seq=2 ttl=64 time=21.465 ms
6. Check SNMP access
Check you can ping the RAN SNMP component (172.18.0.1):
command : # ping snmp
expected result :
ping result OK
For example:
PING snmp (172.18.0.1): 56 data bytes 64 bytes from 172.18.0.1: seq=0 ttl=64 time=23.195 ms 64 bytes from 172.18.0.1: seq=1 ttl=64 time=22.896 ms 64 bytes from 172.18.0.1: seq=2 ttl=64 time=23.204 ms
7. Check LNS access
Check you can ping the RAN LNS component (172.18.0.1):
command : # ping lns
expected result :
ping result OK
For example:
PING lns (172.18.0.1): 56 data bytes\\ 64 bytes from 172.18.0.1: seq=0 ttl=64 time=26.369 ms 64 bytes from 172.18.0.1: seq=1 ttl=64 time=29.609 ms 64 bytes from 172.18.0.1: seq=2 ttl=64 time=25.731 ms
8. Check RAN/VPN connection (dashboard)
Check that the gateway appears as connected to the RAN platform.
command :
Declare your gateway in a fleet (create a new fleet if it does not exist) Follow this link to know how to proceed :Base Station Controller
expected result :
The Gateway should appears with the status: "connected"
For example:
9. Check Packet Forwarding (logs)
Check that the Packet Forwarding is working correctly by analysing the logs.
You should declare a cluster and add a new end-device or using an existing one to check this function.
Follow this link to know how to proceed :Base Station Controller
- For iBTS:
/user/spf2/var/log/ - For iFemtoCell:
/user/spf/var/log/ - For Wirnet Station:
/mnt/fsuser-1/spf/var/log
Check that the gateway has received some messages from the end-device.
For example:
Dec 11 13:17:52 Wirgrid local1.notice spf: INFO: Received pkt from mote: 003EB638 (fcnt=1)
Dec 11 13:17:52 Wirgrid local1.notice spf: JSON up: {"rxpk":
[{"tmst":628163636,"chan":5,"rfch":1,"freq":868.100000,"stat":1,"modu":"LORA","datr":"SF7BW125","codr":"4/5",
"lsnr":8.8,"rssi":-44,"size":19,"data":"QDi2PgAAAQAPkq7BWJzilVB2Lg=="}]}
Dec 11 13:17:52 Wirgrid local1.notice spf: INFO: [up] PUSH_ACK received in 19 ms
Dec 11 13:17:53 Wirgrid local1.notice spf: WARNING: [gps] could not get UTC time from GPS
Dec 11 13:17:53 Wirgrid local1.notice spf: INFO: [down] PULL_ACK received in 25 ms
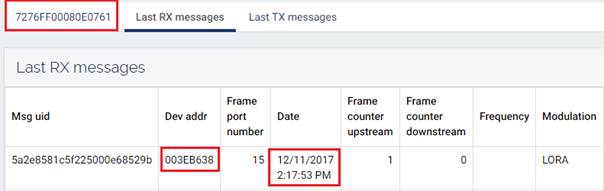
10. Check Packet Forwarding (dashboard)
Check that the Packet Forwarding is working correctly by analysing the uplink messages reported to the RAN dashboard.
Follow this link to know how to proceed :Base Station Controller